DirectAccess
What is DirectAccess?
DirectAccess is a feature built into Windows 7 and newer operating systems that allows users to automatically and securely connect to campus resources when off site.
One of the issues faced by IT staff is managing Windows machines joined to Wolftech that are off campus. The majority of our management is done using group policies, which requires machines having access to domain controllers. DirectAccess will give remote computers secure access to domain controllers when not connected to the campus network.
Requirements
- An IPv6 address
- An update-to-date computer certificate
- The Public and Private Firewall need to be on
Enabling DirectAccess
DirectAccess is enabled by adding a computer or group to a Special Configurations group.
<OU>-SC-Microsoft-DirectAccess-OptIn
Based upon the operating system one of three group policies will be applied:
Windows 7 – NCSU-SC-Microsoft-DirectAccess Windows 7-Clients or NCSU-SC-Microsoft-DirectAccess Windows 7-Clients Centennial
Windows 10 – NCSU-SC-Microsoft-DirectAccess-Clients
Windows 7 machines will also have the DirectAccess Connectivity Assistant 2.0 (DCA) installed. The DCA is used for connectivity troubleshooting and it not needed for DirectAccess functionality.
Multisite Configuration
For load balancing and redundancy there are two DirectAccess servers, one in DC1 and one in DC2. Windows 8 and above operating systems can automatically select the best entry point, but Windows 7 machines have to have a specific DirectAccess server assigned to them, which is the reason for the two Windows 7 GPO’s mentioned previously.
The assignment of Windows 7 machines is done automatically based up on the College they belong to. The assignment were based upon location on campus and the total number of computers in each College.
DC1 – CHASS, COM, COS, DASA, Design, EHPS, OIT, STUAFF
DC2 – COE, LIB, TEX, Delta, Research, Outreach, CNR, CALS
DirectAccess Operation
There is no end user interaction needed for DirectAccess to connect. The connection is established automatically whenever the computer is not connected to the campus next and there is an active internet connection.
DirectAccess determines if it is connected to the campus network by talking to the Network Location Servers (NLS). Only computers with a campus IP address are able to talk to the NLS.
DirectAccess determines what is sent through the tunnel based on the DNS suffix of the destination unlike most VPN software, which uses the IP address of the destination. By default DirectAccess will only send traffic destined for computers in the wolftech.ad.ncsu.edu DNS suffix. This will allow computers to talk to for example the domain controllers and DFS servers.
Known Issues
There may be a slight delay in group policy processing and application if group policies reference servers not using the wolftech.ad.ncsu.edu DNS suffix. For example group policy preferences that map drives or printers located on department file and print servers.
Troubleshooting
DirectAccess creates its own troubleshooting logs in an HTML format that can be attached to a service ticket or emailed to IT staff. Logs are collected from the DirectAccess interface in Settings for Windows 10 or through the DCA in Windows 7.
Windows 10
Start -> Settings -> Network & Internet -> DirectAccess
Click the “Collect” button to start log creation.
If you have a default email client installed Windows will open a new email addressed to activedirectory_sccm@help.ncsu.edu with the DirectAccess logs attached.
If you do not have a default email client, logs are saved in the user local temp directory (e.g. C:\users\%username%\AppData\Local\Temp). The name of the logs will start with the name of the computer you are collecting the logs on and the date/time of when they were collected.
<computer name>-<date/time>-DirectAccess logs.html
Windows 7
From the System Tray right click the DAC icon and select “Advanced Diagnostics”. Log collection will automatically start. Once log generation is completed click on the “Open logs directory” link. By default logs are saved to C:\users\%username%\AppData\Local\Microsoft\DCA\DcaDefaultlog.html
If you have a default email client installed Windows will open a new email addressed to help@ncsu.edu with the DirectAccess logs attached
Manually removing DirectAccess settings
If removing the computer from the DirectAccess Opt-in group does not remove the group police settings applied to the computer, and the computer is no longer able to process group policies or get online the DirectAccess settings can be manually remove from the computer by deleting the DirectAccess registry keys. The registry keys can be found at:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Tcpip\v6Transition
Delete everything under the v6Transition key and reboot the computer.
Also delete all registry keys related to DA under:
HKLM\Software\Policies\Microsoft\Windows NT\DNSClient\DNSPolicyConfig
Delete GPO cache (this folder is hidden):
C:\programdata\Microsoft\Group Policy\History
Delete everything in this folder
Reboot
Adding departmental DNS suffixes
DirectAccess determines what to send through the tunnel by looking at the destination DNS suffix or zone of the traffic being sent. By default only traffic destined for wolftech.ad.ncsu.edu is sent this the DirectAccess connection. This allows traffic for user authentication and group policy processing to be sent through the DirectAccess connection.
Connections to departmental servers needed for group policy processing to map drivers, copy files, or map printers will fail due to being blocked at the campus gateway. Departments can add departmental specific DNS suffixes to their clients to allow for processing of group policies that rely on departmental servers.
DirectAccess determines what to send through the tunnel by looking at the Name Resolution Policy Table (NRPT). The NRPT table can be edited with a group policy:
Computer Configuration -> Policies .> Windows Settings -> Name Resolution Policy
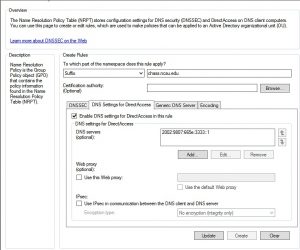
In the Create Rules box select “Suffix” from the drop down box. Next to “Suffix” enter the DNS suffix or zone you want sent through the tunnel.
Select the “DNS Settings for DirectAccess” tab. Check the “Enable DNS settings for Directaccess in this rule” box.
Click Add under the “DNS servers” box. Add 2002:9807:665e:3333::1 in the box and click “Add”
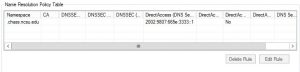
When done, click the “Create” button, and the new rule will be added to the “Name Resolution Policy Table” list.
Repeat these steps until all of the need DNS suffixes have been added. When finish lick the “Apply” button at the bottom.
There is also the ability to add exceptions to NRPT rules. For example if there is a particular server that you do not want accessible through the DirectAccess connection that can be added to the NRPT table as well.
Exceptions are put in using the FQDN of the server. In the GPO instead of selecting DNS suffix from the drop down list select FQDN. In the text box added the name of the server. Select the “DNS Settings for DirectAccess” tab, check the “Enable DNS settings for Directaccess in this rule” box, and click the “Create” button.
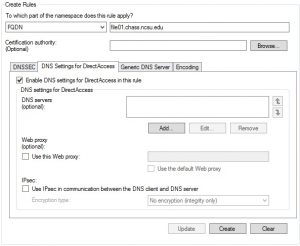
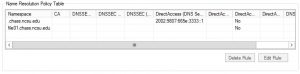
When finished click the “Apply” button.
Scope the GPO to your departmental DirectAccess Optin group.
<OU>-SC-Microsoft-DirectAccess-OptIn
Adding departmental DNS suffixes – Issues
When adding additional departmental DNS suffixes do not add ncsu.edu doing so will cause DirectAccess and other NCSU services to stop functioning.
Powershell Commands
There are a number of useful PowerShell cmdlets that can be used during DirectAccess troubleshooting. A full list can be found here.
Some of the more useful ones are:
Get-DnsClientNrptPolicy – Retrieves the Name Resolution Policy Table (NRPT) configured on the computer.
Get-DAClientExperienceConfiguration – Returns the configuration for the DirectAccess client user experience.
Get-NCSIPolicyConfiguration – Gets information about the Web Probe Host that is used by DirectAccess client computers to verify connectivity to the internal network
Get-DAEntryPointTableItem – Retrieves the list of entry points that have been configured for DirectAccess.